Most Popular API Authentication Methods—Making Sure Clients Are Who They Claim to Be
Businesses are now moving more applications online as a greater percentage of the workforce shifts to collaborating from their home offices. In sync with this transformation, the APIs that integrate those applications are increasingly exposed to external groups—ranging from business units within the company to customers and partners. This exposure not only raises the stakes for protecting users and data but also makes APIs more vulnerable to security attacks.
In this article, we examine the importance of API authentication in making sure only valid clients can access your applications. We also present the key attributes of the most common forms of API authentication so you can select the right one for each of your application services.
What is API Authentication?
Application Programming Interfaces (APIs)—the vital links that allow applications to exchange services and data—require authentication before the exchange can take place. If a client application tries to access another application, the target API wants to know: Is the client really the client it claims to be?
The API authentication process validates the identity of the client attempting to make a connection by using an authentication protocol. The protocol sends the credentials from the remote client requesting the connection to the remote access server in either plain text or encrypted form. The server then knows whether it can grant access to that remote client or not.
That’s essentially what API authentication is all about. The system needs to make sure each end-user is properly validated. The system also wants to make sure the client system does not represent someone who has accidentally tried to access a service they are not entitled to, or worse—the system of a cybercriminal trying to hack into the system.
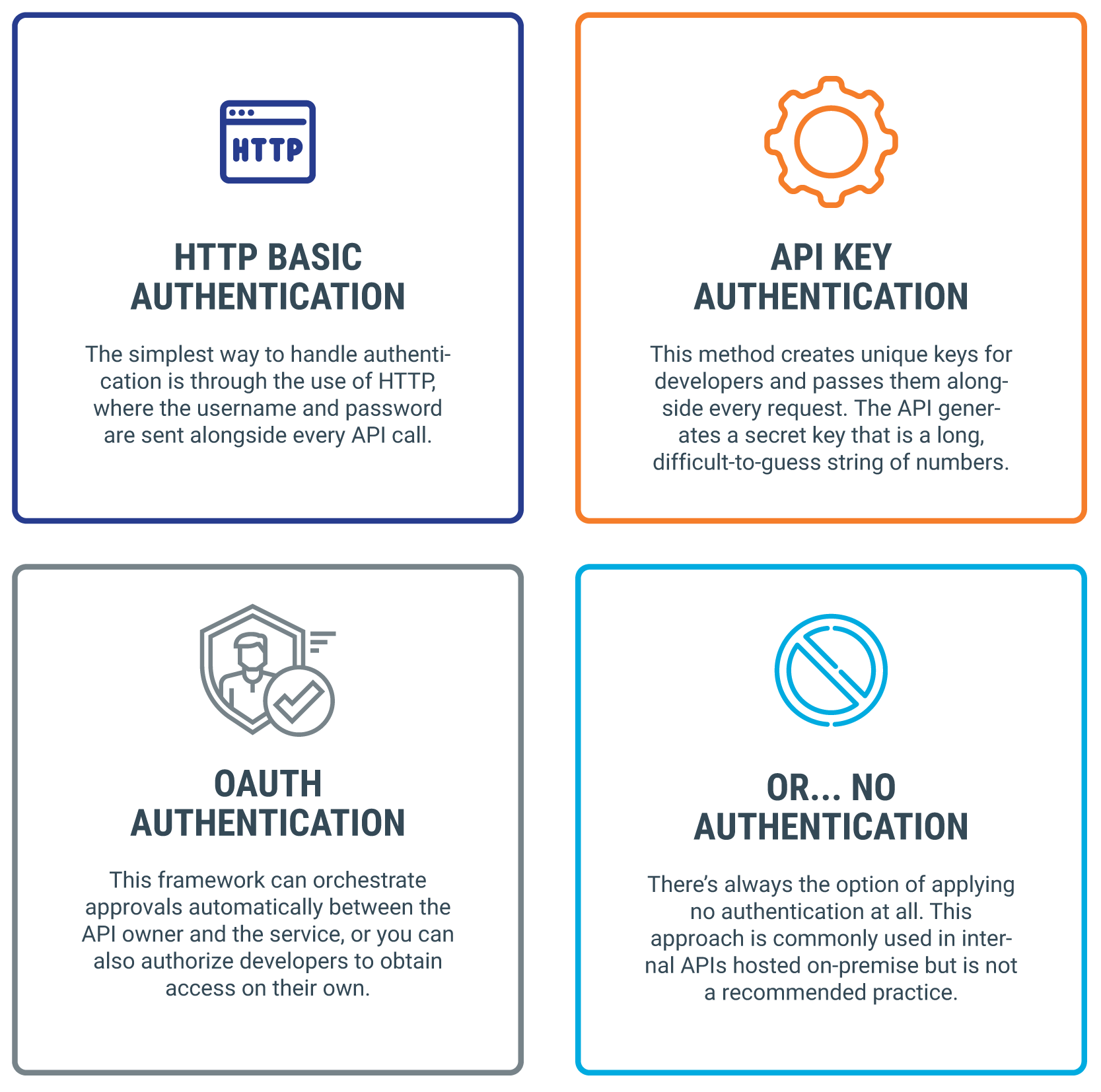
Common API Authentication Methods
There are a variety of ways to authenticate API requests. Here are the three most common methods:
HTTP Basic Authentication
The simplest way to handle authentication is through the use of HTTP, where the username and password are sent alongside every API call. You can use an HTTP header and encode the username and password. Note that does not mean . If you end up using HTTP Basic Authentication, use it through HTTPS so the connection between the parties is encrypted.
API Key Authentication
This method creates unique keys for developers and passes them alongside every request. The API generates a secret key that is a long, difficult-to-guess string of numbers and letters—at least 30 characters long, although there’s no set standard length. It is typically passed alongside the API authorization header.
OAuth Authentication
For HTTP services, you can give third-party developers access by using the OAuth 2.0 authorization framework. This framework can orchestrate approvals automatically between the API owner and the service, or you can also authorize developers to obtain access on their own.
No Authentication
There’s always the option of applying no authentication at all. Developers can just make a request to a specific URL and get a response without needing any credentials or an API key. This approach is commonly used in internal APIs hosted on-premises but is not a recommended practice.
REST API Authentication Best Practices
When setting up authentication for REST API, recommended best practices include adding token validation and avoiding the sending of error messages that disclose sensitive information.
Other important best practices include using SSL, validating the parameters, and avoiding SQL injection.
For APIs that work as products, where multiple external developers can access them, use a combination of a client ID and a private key. Additionally, you can set up a subscription mechanism controlling call rates, access levels and expiration dates.
You should also make sure that the private key can be revoked whenever needed. This can be necessary, for example, when a developer does not adhere to policy requirements, or if a client is no longer in sole possession of the private key due to it being lost or stolen.
[adinserter name=”API-ebook-offer”]
How to Select the Right API Authentication Method
Selecting the authentication method that is best for a particular API comes down to the level of security that’s required to validate clients versus the ease of implementation and maintenance. HTTP Basic Authentication is easy to implement but is also susceptible to account compromise since the password is not encrypted. API Key Authentication is also easy to implement for API providers and application developers.
With a federated system module, OAuth Authentication 2.0 offers security scalability and the best user experience. However, it’s also more work for developers and API providers to implement and maintain. All a user needs to do is click on a button, but the real benefit is that the user can utilize an existing account, and the app developers can leverage an existing authentication mechanism, which is less work than creating one on their own.
Another tool to consider that complements OAuth 2.0 is OpenID Connect. It works as an identity layer you can deploy on top of the protocol so the API can verify a client’s identity and profile via authentication performed by the authorization server.
With the combination of OAuth 2.0 and OpenID Connect, you thus benefit from a stronger security posture—a system that natively supports strong authorization in addition to embedded authentication methods. This decreases the cost of implementation over the long run.
Don’t Just Give Access to Anyone
An important concept of web API authentication to understand is that it’s not the same as API authorization. While authentication first validates the identity of a client, authorization then verifies that a connection to a particular application operation is allowed. Within a given application, you may limit clients to certain operations.
Finding the right level of authentication for your APIs is vital. When you open up your applications to external software developers, you don’t want to just give away access to application services to anyone. You want to employ authentication mechanisms to ensure only the applications and systems that should have access are actually able to make a successful API call to your application services.
[adinserter name=”API-Closing”]
[adinserter name=”Platform Modernization Promo”]
Recent blog posts

Stay in Touch
Keep your competitive edge – subscribe to our newsletter for updates on emerging software engineering, data and AI, and cloud technology trends.