Data Analytics Cybersecurity Best Practices
As businesses increasingly embrace new opportunities offered by Big Data and the interconnected network of IoT devices and systems, new opportunities are also emerging for cybercriminals to exploit them. One unsecured endpoint can take down an entire system in a matter of seconds.
While there’s no shortage of security issues in Big Data analytics, these technologies also hold the key to protecting businesses against incoming threats from inside jobs to phishing and from weaponized cloud services to supply chain attacks. Insights provided by Big Data analytics tools can be used to predict, detect, and contain cyberattacks before they do any major financial, reputational, or even physical damage.
Below, we look at some of the best practices for fighting Big Data’s security challenges with more Big Data solutions.
The Need for Big Data Analytics for Cybersecurity
As the amount of data continues to grow at an explosive rate, cybersecurity tools need to keep pace. Otherwise, organizations find themselves exposed to serious risks. And it’s not just cybercriminals and data breaches. A 2019 IDG Cybersecurity Priorities Study of 528 participants revealed the following:
- 59% reported that protecting personally identifiable information (PII) is a top priority due to GDPR and CCPA regulations.
- 44% said they would like to increase security awareness training to reduce instances of identity theft and phishing in their organization.
- 39% believed that improving data security and IT infrastructure will improve business resiliency.
- 24% want to use Big Data analytics responsibly.
- 22% said that they would like to reduce the complexity of their organization’s security infrastructure.
As you can see, the IDG report found that issues like compliance, internal threats, and learning to use Big Data responsibly are major concerns that brands are currently grappling with as they embrace new solutions.
A 2019 CrowdStrike report highlighted another critical concern: threat detection. Researchers found that 95% of respondents fail to meet the standards of the 1:10:60 rule. What this means is, based on respondents’ current capabilities, it takes an average of 162 hours to detect and contain a data breach.
CrowdStrike also found that 80% of participants reported being unable to stop one or more attacks on their networks in the past year. 44% said that slow threat detection was the reason for the delay.
Another challenge is that organizations have trouble making sense of cybersecurity data.
According to a joint survey by Big Data LDN and Cloudera, The Fourth Industrial Revolution, 45% of data leaders reported that data visualization is the biggest barrier to achieving target objectives.
Big Data analytics tools can help companies get ahead of their biggest cybersecurity challenges—from maintaining compliance across distributed networks and high-volume data sets to detecting threats as they emerge. In addition, real-time, AI-enabled analytics tools can provide system-wide visibility and solve issues like slow detection or failing to contain threats before they spread, saving organizations significant time and money.
Some solutions transfer real-time data into maps that update as conditions change, helping organizations visualize cyberattacks by type, area, or the location of a cyber attacker’s servers. Other AI analytics tools analyze data as it comes in, then recommend next steps for cybersecurity teams to follow.
Best Framework for Building a Big Data Analytics-Cybersecurity Strategy
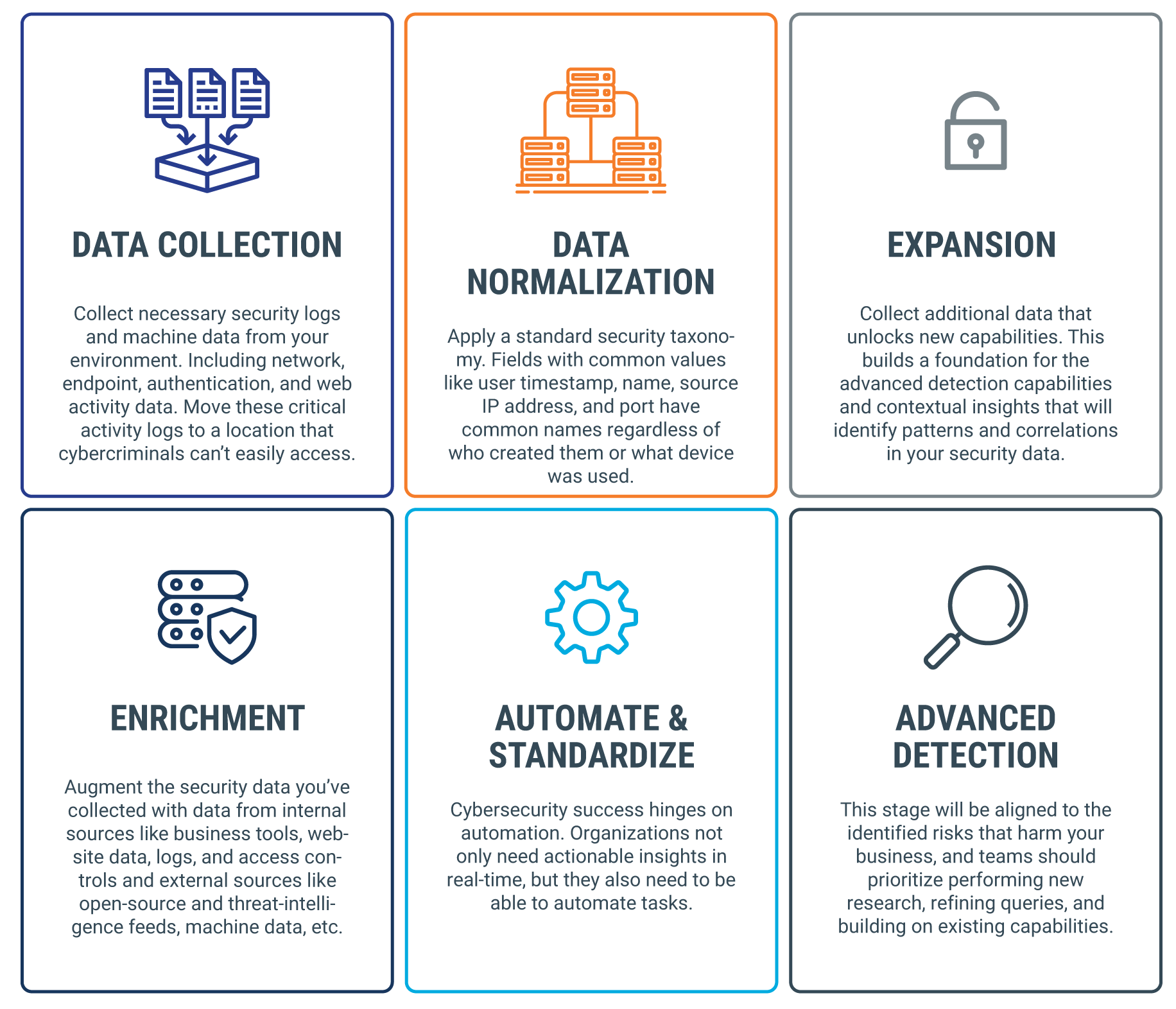
While there’s a lot of variation when it comes to data analytics cybersecurity strategies, there are some general best practices that tend to apply across the board. Here’s a basic framework that lays out the steps organizations should take to build a foundation for an effective, scalable program—regardless of use case.
- Data Collection. The first step is to collect the necessary security logs and machine data from your environment. This includes collecting network, endpoint, authentication, and web activity data, then moving those critical activity logs to a separate location that cybercriminals can’t easily access. At this stage, you also need to collect the raw data required to gain an understanding of the security environment and perform basic investigations.
- Data Normalization. As you combine the data collected in the last stage, your next goal is to apply a standard security taxonomy. This means that fields with common values—like user timestamp, name, source IP address, and port—should have common names regardless of who created them or what device was used. While it might sound like a simple step, establishing universal naming conventions enables organizations to streamline search capabilities, develop a unified view of the threat landscape, and define common terms for discussing security issues.
This is a critical step for detecting threats across a wide range of sources and sets you up to scale your data-driven cybersecurity capabilities.
- Expansion. Building on the last step, expansion involves collecting additional data that unlocks new capabilities. Here, you’re aiming to build a foundation for the advanced detection capabilities and contextual insights that identify patterns and correlations in your security data.
While you’ll now be able to spot some common indicators of compromise, much of this data lacks context at this stage and may contain undetected indicators that could put your system at risk.
- Enrichment. At this step, your goal is to augment the security data you collected thus far with additional intelligence. This means pulling data from internal sources like business tools, website data, logs, and access controls and as well as external sources like open-source and threat-intelligence feeds, machine data, and others.The idea is to create the end-to-end visibility that allows your cybersecurity team to detect security events and incidents sooner. You want to establish alerts that indicate the severity of incoming threats and gain the capability to detect threats and gather contextual information about each incident.
You will now have sophisticated detection capabilities, but teams might not have what they need to connect security insights to big-picture business goals. Additionally, you need a system for measuring performance and recording contextual insights that can be used to refine your cybersecurity strategy.
- Automate and Standardize. In the world of Big Data, cybersecurity success hinges on automation. Organizations not only need actionable insights in real-time, they also need to be able to automate tasks.
Automation can ensure that data becomes available faster and is sent to the right people as needed, and that your system can automatically act when a cyber threat is detected. Additionally, this allows analysts to categorize cyberthreats without causing delays that could prevent companies from leveraging time-sensitive data for value-driving activities. At this stage, organizations should be able to monitor their environment continuously for incoming threats and act accordingly.
Where the previous steps involved collecting and organizing data, here you start putting it to work. While it depends on your security goals, that might mean tracking incidents, scanning for vulnerabilities, or automating simple response actions.
- Advanced Detection. It’s all about continuous improvement, which means culture plays as much of a role as the data sets and technologies you use to protect your system. This stage aligns to the identified risks that harm your business, and teams should prioritize performing new research, refining queries, and building on existing capabilities.
Big Data analytics—along with network flows, logs, and system events—can detect anomalies and vulnerabilities in your system that put your organization at risk. Still, success requires accurate information and actionable insights. It also means you need to act on threats as needed and route critical information to the right person.
For the long term, look into applying machine learning (ML) across the entire threat spectrum. This Cisco report breaks down the process of ML threat detection and evolving capabilities over time. A basic ML program can automatically detect known-known problems, or problems you’re already familiar with. Over time, it can be used to detect known-unknowns, which identifies issues that share characteristics with known-known problems.
The end-game, however, is a system that can detect unknown-unknowns. This means that your system can detect unrelated malware or unusual behavior even if it’s never encountered anything like it.
Big Data Analytics Cybersecurity Tools
Big Data analytics tools can help organizations analyze high-volume, high-variety, high-velocity data, allowing them to identify threats in real-time. Organizations considering a Big Data solution for cybersecurity might look into the following tools. However, it’s worth pointing out that your tech stack will depend on your system and goals for your cybersecurity program.
- Endpoint protection platforms are deployed on endpoint devices to prevent malware attacks, detect potential threats, and respond to and investigate incidents. Most solutions are managed in the cloud and support continuous data collection, monitoring, and the ability to control the device remotely.
- Security Information and Event Management (SIEM) platforms collect logs and event data generated throughout an organization’s infrastructure and provide analysis and alerts based on pre-defined business rules. Some solutions offer information security data analytics—with PCI DSS, GDPR, and CCPA compliance controls and monitoring. You might also look for platforms that offer data visualizations and integration with third-party feeds.
- Threat intelligence software gives organizations information about cyber threats such as new malware, zero-day attacks, malicious IP addresses, and unusual activity happening around the world. These tools provide security analysts information to go ahead and prevent being hit by a new threat.
- Fraud detection usually comes into play for financial services companies that need specialized threat assessment tools to detect fraud accurately in real-time. Systems usually analyze user behavior, IP addresses, risk appetite, and even more sensitive matters, like whether a user has substance abuse issues.
- Predictive modeling offers AI-enabled solutions that enable data science experts to build models to get ahead of cyber threats before they happen. Machine learning solutions can learn to detect unknown indicators that there’s a potential threat on the horizon and issue an alert to help teams get prepared.
- Anti-malware sandboxes provide an environment for analyzing malicious files in a virtualized environment, allowing users (or their AI) to learn more about how malware behaves as it executes. Teams can use these tools to automate malware analysis and use those findings to inform prevention strategies moving forward.
Cybersecurity Data Analytics Quickly Becoming a Business Requirement
By analyzing Big Data, businesses can prevent, detect, and even predict emerging threats, including ransomware attacks and compromised devices. Big Data analytics tools with embedded AI and machine learning capabilities allow organizations to get ahead of cyberattacks, reduce threats from the inside, and maintain compliance with data privacy standards.
Without Big Data analytics tools, it wouldn’t be possible to capture and analyze every data point that could reveal a weak spot in the network. But with the data coming from IoT devices, an increasing number of communications channels, transactions, logs, and business applications, machine learning, automation, and natural language processing are becoming critical elements of any Big Data cybersecurity strategy.
[adinserter name=”Data Analytics CTA”]
Recent blog posts

Stay in Touch
Keep your competitive edge – subscribe to our newsletter for updates on emerging software engineering, data and AI, and cloud technology trends.