Mitigation Strategies to Address IT Security Risks
“Sony Corp’s Executive Deputy President Kazuo Hirai speaks at a news conference to apologize for a massive security breach of its Playstation Network in Tokyo,” May 1, 2011.
“Hackers have stolen more than 225,000 Apple accounts from iPhone customers,” CNNMoney (New York), September 1, 2015
“2014 cost of a data breach: Average $3.5 million,” Ponemon Insititute, May 5, 2014
In today’s fast paced global economy that depends majorly on data and information, ensuring the security of IT assets has become paramount. Based on recent research by CompTia, 28% of today’s businesses list security as a highly important factor, a number that is predicted to increase within the next two years. The study also claims that many companies that believe they are sufficiently secure are actually potentially vulnerable to major security threats emerging with new technologies. These rising threats are encouraging businesses to adopt new approaches to address these changing security needs. In another survey done by Gartner, research indicates that mobile is now a rule, not an exception, for most of the companies.
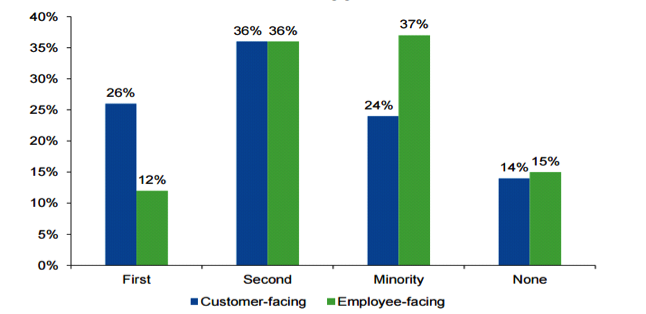
The research was conducted with CIOs being asked, “How would you select an approach, with respect to mobile, when designing both customer- and citizen-facing apps and services and employee-facing apps and services?” They were then given the following options:
- By default, we design the experience around a smart mobile device as the primary interface
- We always factor in design for mobile, but normally as a secondary interface
- We only consider mobile for a minority of services, where we know it is necessary
- Mobile is rarely a consideration for us
The results found that 26% of the customer facing and 12% of the employee websites were considering mobile as primary platform. The percentage of companies considering mobile as secondary medium was also quite high. These data points indicate that mobile has become a priority across companies where it wasn’t in previous years.
So what is making mobile security paramount?
15 years ago
15 years ago, there were only a limited number of company devices used for accessing company emails and other company applications, which were pretty much locked down. This means that the attack surface was quite limited.
Today
Today, the devices connecting to companies are based on multiple OSs with highly rich functions. This makes the attack surface hard to manage in terms of predicting how to use these devices, so assuming the application of common practices will always work becomes a big concern.
2 years from now
As we go forward, minimum IT policy control will become the norm because there will be so many non-company devices. Also, the emergence of the Internet of Things will guarantee that everything bought in the future will have some kind of microprocessor in it, as well as be network addressable.. This will further enhance the attack surface, which will leave our IT assets more vulnerable to security threats such as an advanced persistent threat and malware defenses. This write-up deliberates upon six proactive industry practices and guidelines which can make an organization’s IT assets secured enough so that such vulnerabilities don’t happen in the first place.
1. Keep system patched and updated
Most system failures happen due to a lack of proper patching. Here are some statistics from researchers, which describe quite interesting facts about some common vulnerabilities faced by organizations:
| Zero Day Attack | 1% |
| State-Sponsored Attack | 2% |
| Attack due to patches available for less than a year | 7% |
| Attack due to patches available for more than a year | 90% |
The most interesting observations from the above statistic are:
- 90% of the attacks happen due to not applying the patches that are older than a year
- If an organization is performing standard maintenance on all systems, then the attack surface reduces to 3% or less
Furthermore, if an organization supports BYOD and loses control on performing standard maintenance, then the problem gets worse because they are inviting more attack sources without much prevention. To avoid this risk, make sure all of the systems are up-to-date, including the servers inside the company, laptops, desktops, and mobile devices. Smaller mobile devices come with a variety of operating systems, firmware, etc.; considering this, organizations should ideally allow only those mobile devices for which patches can be maintained.
Reactive Vulnerability Management:
Having a vulnerability management program (such as QualysGuard), organizations can protect themselves from Heartbleed-type vulnerabilities and take a reactive approach to mitigate risks as they exist in their environment.
Proactive Vulnerability Management:
Along with a reactive approach, it is essential to identify, assess, and respond to new threats before they become a reality. This can be achieved through some of the proactive vulnerability management programs. Some of the popular proactive vulnerability management tools, such as Secunia help to perform patch management. Proactive Vulnerability management tools scan an organization’s entire IT assets and provide a vulnerability report, which indicates the missing patches and updates based on the latest security advisories provided by Software majors such as Microsoft, CISCO, and Adobe.
2. Anticipate and allow only a limited fragmentation of OS in order to reduce maintenance complexity
It is nearly impossible to maintain patches for all of the mobile models given the variety of operating systems available in the world. Let’s analyze OS fragmentation between Apple iOS and Android, as published by Gartner.
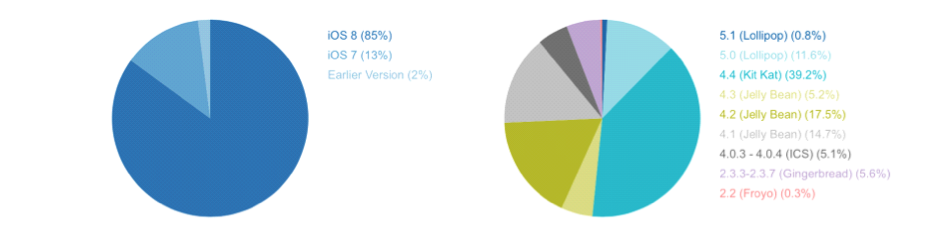
| Apple iOS | Android |
| 85% of the devices are on iOS8, which is the current version | 48% of the devices are fragmented and running on obsolete and vulnerable versions |
| iOS has consistent updates | Update not certain |
There are more than 24,000 versions of Android devices in the market; this is because each version of these smartphones (such as Samsung Galaxy S3, S4, etc.) has various carriers, and each carrier modifies the firmware, startup dialog, default setting, etc. of the mobile devices. Even Google-certified devices are not guaranteed to be secure because Google doesn’t certify that encryption is in place. Apple, on the other hand, keeps iOS from becoming so fragmented. Considering this, organizations should allow only a limited number of Android-based devices for a BYOD program, which can be patched. By having such a policy, the complexity to maintain patches for different versions of Operating Systems would reduce substantially.
3. Apply Pareto Analysis to identify key mobile security challenges
The majority (mostly 80%) of the risks are due to very few issues, which was drawn by the information discovered by the following research reports:
- Almost 25% of computers are still unprotected from viruses and malware (By Microsoft)
- 90% of Windows 7 flaws were fixed by removing admin rights (By Ars Technica)
- in 2013, 99% of mobile malware was aimed at Android (By F-Secure)
- 80% of banking customers not using a bank’s mobile platform said it was because they are skeptical about the mobile application’s security (ByLunabee)
Through the Pareto analysis, we can find out the key issues that can trigger potential risk.
This Pareto analysis is most beneficial when applied on the right parameters. The following statistics describe the two types (Tickets per month & Cost to close) of analysis done on a company’s ticket data.
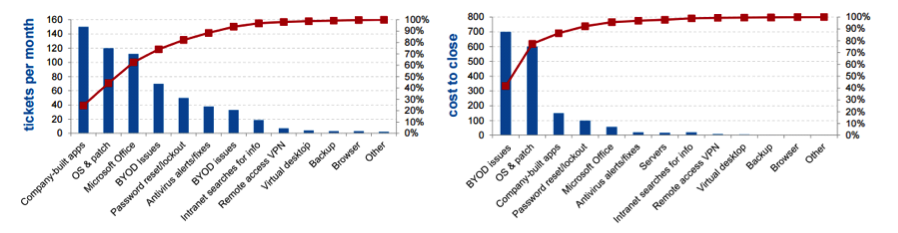
According to the left hand chart, “Company built apps,” “OS & Patch,” and “Microsoft Office” appear to be the most critical because the highest percentages of tickets belong to these ticket buckets. However, the second analysis, done on same data but with a different parameter—cost to resolve the tickets—found that tickets belonging to BYOD issues and OS and patches are the most expensive to fix and thus should be given more attention. So although companies build apps, tickets are still the numbered majority; however, they are quite easy to fix and do not require much effort.
So by applying this Pareto analysis, we can identify the most concerning factors and control them on priority.
4. Handle BYOD carefully; policies for BYOD should be in place even though it is not intended
A company should never ignore BYOD, even if they do not officially support it. Mostly companies expose their exchange or internal applications via the Internet; in such cases, users may practice BYOD without employer knowledge and/or without any rules, which increases the attack surface. As a solution, companies can restrict the access of applications by issuing security certificates to the intended users. By doing this, if any employee/user loses the device or sells it, they can inform the company and the certificate can be disabled.
5. Conduct governance reviews and mobile security assessments regularly
Governance reviews and assessments are essential to measure and define the operational efficiency of the IT operations, as well as to find out the gaps that need to be fixed. Popular research companies such as Gartner and OWASP offer security matrices to perform security assessments and to identify the IT security maturity level of the companies.
IT Score is a popular assessment matrix from Gartner that helps organizations to identify risks and measure and understand their company’s mobile security program maturity. For example, in the Spider charts below, the chart on the left indicates a company’s present score, while the chart on the right indicates what should be the ideal score for the company.
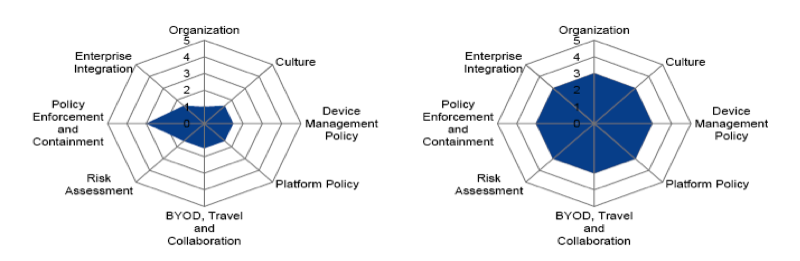
This kind of assessment from a third party can also help to identify the right parameter for performing the Pareto analysis.
6. Define common security policies for all types of devices
Due to the emergence of a variety of devices that can access a company’s confidential information, it is essential to implement common security policies for each type of device. A few of the common rules are:
a. PIN requirement for all devices: In the Healthcare industry, HIPPA policies require PIN security features to be implemented on all devices that could potentially hold any type of electronic patient health information.
b. No jail break rule: Do not give access to the core functions of the phone, such as the root for Android.
c. Mandatory security certificate to access applications: Applications should be made accessible only via certificates, regardless of device-type.
d. Allow only approved models and versions: Only limited models and versions recommended by security consultants should be allowed to access the company’s confidential information or should be allowed for BYOD.
e. Remove users who move to non-prescribed device models and OSs or who install insecure applications: Most malware comes into mobiles if they are accessed from non-prescribed locations (such as from outside Google store or Apple store), so if users install applications from these sources then the certificate should be disabled.
f. Perform security testing: Perform both SAST and DAST (Static and Dynamic security testing) to capture maximum vulnerabilities in applications both from inside and outside.
g. Ensure API Security: In order to comply with stringent enterprise and government mandates, it is essential to perform API Security.
h. Adhere to standard programming practices: A few such practices are:
- Weak Server Side Controls: The servers where apps are hosted should have security measures in place to prevent unauthorized users from accessing data.
- Insufficient Transport Layer Protection: Prefer TLS over SSL for better transport level security.
- Client-Side Injection: Native mobile applications should be protected from all types of injections attacks because client code resides locally. Identify such issues through SAST and DAST.
- Improper Session Handling: Sessions on mobile applications should be timed out if they are not accessed for a certain amount of time.
- Use Untrusted Inputs Carefully: Inputs such as cookies, environment variables, and hidden form fields can be modified by attackers, so it is essential to encrypt the data for such variables.
- Side Channel Data Leakage: This happens when mobile developers fail to notice that the cryptic data is not cleaned from the local cache or log, or that it is being captured by Operating system itself. This is then decoded by attackers and causes a data leakage.
- Broken Cryptography: It is essential to ensure that the encryption applied is up-to-date, stable, and not yet broken.
Conclusion
The most precious asset of any organization is reputation, and security is the most important goal. This can be achieved only by having standard security policies in place; however, even the best security policy is useless if end users fail to or refuse to adhere to the policy.
Recent blog posts

Stay in Touch
Keep your competitive edge – subscribe to our newsletter for updates on emerging software engineering, data and AI, and cloud technology trends.